More and more public safety agencies are moving to trunked radio systems, making it difficult for scanner listeners to follow the action. Newcomers to trunking need a good introduction to all the terminology and equipment, and even old hands have a question now and then. So whether you're new to scanning trunked systems or you've been doing it for a while, Tracking the Trunks will guide you through the maze of current and future trunking systems.
What is Trunking?
"Trunking" is a word borrowed from the telephone system to describe a large number of users sharing a much smaller number of communication paths. The wires from your home telephone, along with hundreds of others, connect to a local "central office." Your central office connects with other central offices around the country by way of "trunks," which are really just pairs of copper wires (or these days, strands of glass called fiber optics).
When you pick up the phone and place a long distance call, your central office assigns one of its idle trunks to your call, linking you to the destination central office. That trunk remains dedicated to you for as long as your call lasts. When you finally hang up, the trunk returns to idle and is available for another call.
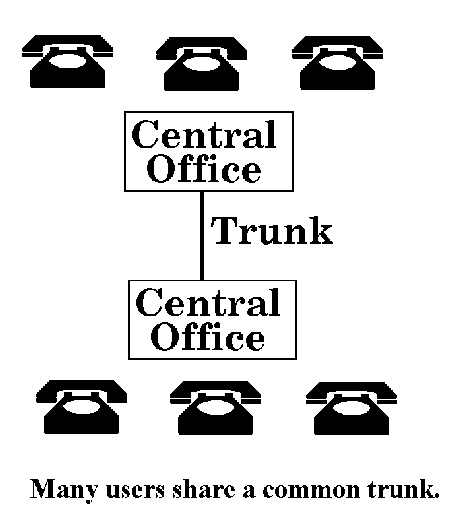
Because your phone sits idle most of the time (unless you have teen-aged children), just like all the other telephones in your neighborhood, the telephone company doesn't have to go to the expense of having a trunk between central offices for every telephone. Since any particular telephone only needs a trunk while a call is in progress, the phone company can share these trunks among all the telephones. By examining the average and peak number of calls made through your central office, the phone company can figure out how many trunks they actually need. This number will be much lower than the total number of telephones, since they only need enough trunks to prevent someone from getting an "all circuits are busy" message.
As an aside, this plan worked fine until telephone calls started lasting several hours rather than the usual ten or twenty minutes. Planners at the phone company didn't expect long modem calls to Internet Service Providers, and so many exchanges began running out of idle trunks in the early evening during prime web-surfing hours. This is also why it's so difficult to get through to areas that have suffered from earthquakes or other natural disasters. Even when the phones are working, all of the trunks connecting the local central offices to the outside world are in use as frantic relatives try to reach their loved ones.
In the case of radio, the scarce resource is not wires, but frequencies. To illustrate the problem, at any particular time in a large city like Los Angeles or Chicago there are hundreds of police officers on duty who all need to stay in contact with a dispatcher. If each officer had to have his or her own exclusive radio channel, we'd run out of room in the available frequency bands before we could equip everybody. It would also be very wasteful, since those radio channels would be idle most of the time.
"1 Adam 12"
So historically these departments use a handful of radio channels, with one chosen as the common dispatch channel that all the mobile users tune to and listen for their call sign. Everyone can hear everyone else on the channel, and everyone has to wait for his or her turn to speak. Remember the television show "Adam 12"? Los Angeles Police Officers Malloy and Reed had to listen for their call sign on the dispatch channel, which was often very busy. "1 Adam 12, 1 Adam 12, see the man, 1451 Western Avenue." Radio messages had to be kept short, since many other patrol cars were also listening to the channel, waiting for their turn to be called or to radio in a report. When a conversation was more involved, the officers were told to "switch to Tac-2," where Tac-2 (tactical channel two) was a different, less busy frequency that could be used without delaying other urgent radio messages on the main channel.
Because all the patrol cars had to first use the dispatch channel, if an officer had an important message to deliver while another car was using the channel, they would have to wait. It would be helpful to allow the waiting car to immediately use Tac-2, or some other idle radio channel, to get the message through more quickly.
This is the idea behind trunking.
Waiting for Service
Imagine waiting with a group of friends for a table at a crowded restaurant. You go up to the hostess and give her your name, and she puts it on a list with a bunch of other names. If all the tables already have people at them, you wait. When a table is ready the hostess announces your name over the loudspeaker and you and your friends follow her to the table she selected for you (probably the first one that became available).
The operation of a trunked radio system is very similar to this crowded restaurant. You and your friends are in a "talk group," and when you want to talk to your friends you first have to request a channel assignment from a computerized "hostess" that runs the system. The computer will make you wait until a channel is free, then publicly announce your "name" (really your talk group) and the assigned channel that it selected. You and all your friends then switch to that channel and you can proceed with your conversation.
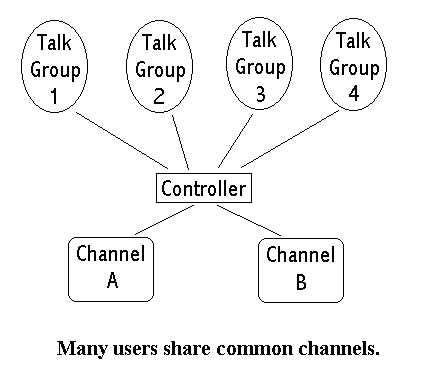
Fundamentally there are two types of trunking. The first, called message trunking, is when the same channel is held for the entire conversation. This is usually done just for telephone calls or other special communications, and is the norm in cellular telephone systems.
The more common type is transmission trunking, where the channel is held only for the duration of one transmission. A conversation that takes place over several transmissions may actually occur on several different radio channels because the controller may assign a new channel every time someone presses their push-to-talk button. This is the most efficient way to share radio channels, since other people can use the channel during pauses in the conversation, but it's also what makes it so difficult for a normal scanner to listen in.
Trunked radio channels carry two types of information. The first, obviously, is the voice portion of the conversation, which can be in either analog or digital format. Analog is currently the most common, so it's readily discerned with existing hobby equipment, but several manufacturers of trunking systems are selling digital voice systems as well. We'll dig into these newer, more complex networks in later columns.
Trunked radio channels also carry control information, which is really just digital data shared between mobile radios and a computerized controller. This data includes channel and user identification information that must be decoded before it can be used.
Encoded versus Encrypted
As another aside, let's clarify the difference between information that is encoded and information that is encrypted. Encoding is simply a way of expressing something in a different way for efficiency or reliability or some other technical reason. For instance, these days when you receive a letter from the Post Office you'll see a series of short and tall bars stamped near the bottom of the envelope. Those bars are just an encoded form of your zip code - nothing mysterious or secret, and anyone can decode those bars if they have the coding specification from the Post Office. Encryption, on the other hand, is the deliberate scrambling of information for the purpose of protecting the contents or meaning of the message. Encoding and encrypting are two different things, despite some attempts by manufacturers to equate the two.
In the trunked systems we'll be covering in this column, the control channel information is simply encoded, not encrypted. The specifications that describe the format and content of these channels are available, and companies have used that information to produce products in a legal manner.
In the United States, trunking occurs mainly in three frequency bands. The first, and most popular with new public safety systems, is the 800 MHz and 900 MHz bands. Second are networks in the 450 MHz band, commonly referred to as UHF (Ultra High Frequency). In addition, there is some trunking activity around 150 MHz (also known as VHF or Very High Frequency). The Federal Communications Commission (FCC) limits trunking operations below 150 MHz, in their words, "¼ because, given favorable propagation conditions, signals on those frequencies can cause interference to stations hundreds or thousands of miles distant."
Trunking Equipment
So, what do you need to listen to these signals?
By far the easiest way is to purchase a scanner that is capable of tracking trunked conversations in these bands. There are nearly a dozen different scanners currently on the market that meet this requirement, almost all of which are available from reputable equipment dealers. Detailed reviews of these radios may be found in current and back issues of Monitoring Times magazine.
If you're looking for a handheld unit, Radio Shack markets the PRO-91, PRO-92, and PRO-94. Uniden also sells the Bearcat 235XLT and 245XLT radios. You may also run across a PRO-90, which is an older trunk tracker that doesn't appear in the current Radio Shack catalog.
For desktop listening, Radio Shack markets the PRO-2050 and PRO-2052, as well as the mobile PRO-2066. Uniden sells the Bearcat 895XLT.
If you have a computer and want to go beyond the limits of a normal scanner, there are a variety of options ranging from finished products to homebrew solutions. Optoelectronics in Ft. Lauderdale, Florida, sells their OptoCom computer-controlled receiver, which uses software on your personal computer to track the most common types of trunked radio systems, as well as conventional signals. If you already own an Icom or AOR receiver, Optoelectronics also sells an add-on device called the OptoTrakker which will allow you to track trunked radio systems.
You may also use a small external circuit called a data slicer to deliver data into your computer, which can decode trunked signals using public domain software programs. These circuits are commercially available as stand-alone boxes or built into larger devices, but require a signal from your receiver called the discriminator output.
Stay Tuned
We'll take a detailed look at all of these equipment and software options in upcoming columns, as well as examining specific trunking systems, their frequencies and related information. For those readers who are already following trunked systems, I'd love to publish frequency lists and talk group assignments that you've worked out.
In the meantime, you're welcome to send me electronic mail at dan@decodesystems.com, or check my website at http://www.decodesystems.com. Until next month, happy monitoring!