Most Americans are much more security conscious now than they were before the terrorist attacks on September 11, 2001. A number of new laws have been passed in the wake of the attacks, many geared toward giving government agencies further latitude in pursuing persons suspected of criminal activity. In such an environment it shouldn't be a surprise that the following message appeared in Internet news groups:
The National Security Council and the FCC quietly asked Uniden to cease production of an APCO 25 digital scanner for the time being. The National Security Council cited security issues in the request due to the fact that many military and police agencies, border patrol and INS are unencrypted APCO 25. Uniden representatives will not even discuss the issue for fear that the NSC might also pressure Uniden to halt production of the BC-780...
By way of background, in early 2001 Uniden reported that they were working on a scanner that could monitor the digital voice transmissions from APCO 25 radios. Although Uniden's intended use for such a device is the legal monitoring of public safety agencies, many federal police and some military units also use APCO 25 equipment. Since no such scanner is currently available to the general public, APCO 25 users have a modicum of privacy from the casual listener. (It should be noted that a dedicated hobbyist could monitor APCO 25 signals for well under $2000, a small amount of money even for a poorly-funded terrorist organization.)
In response to this note and numerous requests, Uniden issued this statement:
Uniden America Corporation is developing an APCO 25 digital scanner model, which is slated for distribution in the fourth quarter of 2002. To date, and contrary to industry rumor, Uniden has received no requests from the FCC or any federal, state, or local authority asking the company to delay or halt development of this or any other Uniden product.It is important that the public understand the nature of APCO 25 scanner technology, which allows users to pick up ordinary digital signals such as those now used by police and emergency officials in a few large US cities including, for example, Los Angeles. Scanners such as the APCO 25 model in development by Uniden do not facilitate the decoding of any encrypted transmissions including transmissions by national security and law enforcement authorities such as the CIA, DEA and U.S. Special Forces Units.
Uniden at this time does not anticipate receiving any requests to alter its product-development schedule on any APCO 25 digital scanner units.
Jennifer Ainsworth
Media & Trade Show Manager
Uniden America Corporation
4700 Amon Carter Blvd.
Fort Worth, TX 76155
Encoding Versus Encryption
While it is generally against federal law in the United States to monitor encrypted transmissions, at the moment it remains legal to monitor most encoded signals (some signals are strictly off-limits regardless of their characteristics -- for example, anything in the cellular telephone frequency bands is forbidden).
At first blush, encoded and encrypted signals sound the same coming from an ordinary scanner. You may have heard the harsh grinding or "hash" noise from an open squelch when tuned to a digital signal, such as the control channel of a trunked radio system. Not all digital signals sound the same, of course, but no one can tell by ear whether an APCO 25 transmission, for instance, carries voice that has been encrypted. The only way to find out is to decode the transmission as far as possible and see if what remains is encrypted or not.
A code is simply a way of representing something, and all digital messages transmitted over radio use some kind of encoding. Digital implies that the message is made up of a sequence of binary 1's and 0's, and the way in which that sequence is transmitted is the encoding method. Some code representations are very simple, such as the signal from your garage door opener, and some are rather complex, such as APCO 25.
Newer garage door openers have a "security setting" that is encoded in the transmission from your car to the garage. The transmission itself is a representation of the security setting. The receiver inside the garage decodes the transmission, translating the representation back into the security setting. Encoding and decoding are necessary to get the message from the transmitter to the receiver in a reliable and efficient manner. There is nothing hidden or secret going on, so all of this is separate and distinct from encryption.
APCO 25 messages are much more complicated than garage door opener signals, but at a fundamental level they follow the same process. The message to be sent, a snippet of digitized voice, is wrapped with error correction and signaling information before being transmitted. At the receiver the signaling information is peeled off and the error correction data is used to eliminate the effects of any interference that may have occurred. The result is the original digitized voice, which was encoded but never encrypted, and should be legal to monitor.
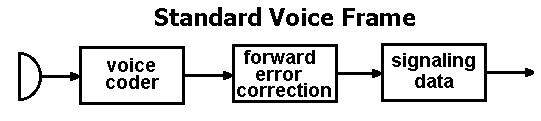
Of course, the owner of an APCO 25 system may choose to encrypt the snippets of digitized voice within the encoded transmission. This adds cost and complexity to each radio but in many systems is already in place for sensitive talkgroups such as detectives and SWAT teams. In these cases the hobbyist listener is out of luck.
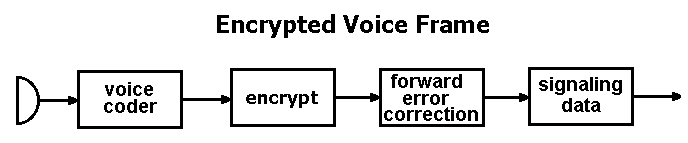
Encrypted Voice
APCO 25 isn't the first type of system to have encryption.
Many early systems offered a cheap, easily defeated analog method known as voice inversion scrambling. In this scheme the band of audio frequencies used for human speech is split into two parts, a lower block and an upper block. The blocks are inverted before transmission and inverted once again (restoring the original arrangement) at the receiver. Anyone overhearing the transmission just hears the "Donald Duck" noises as the user speaks. Both hardware and computer software to undo this type of scrambling are available to hobbyists these days, and it is even possible (with practice) to understand inverted speech with no mechanical aids at all.
Motorola Voice Encryption
Since the 1970's Motorola has offered digital voice encryption on their two-way radio products, either built-in or as an add-on device. The first capability was termed Digital Voice Privacy (DVP), which at the time was intended to provide a basic level of privacy for businesses and local governments. The method of encryption used in DVP is based on a proprietary algorithm kept secret within Motorola. It uses a 32-bit key, which these days doesn't provide much protection.
For a higher level of security the DVP algorithm could be replaced by the Data Encryption Standard (DES), which follows the federal standard put out by the National Bureau of Standards (now the National Institute of Standards and Technology, or NIST). DES is well-known and publicly available algorithm that uses a 56-bit key, although for modern uses it has recently been replaced by the Advanced Encryption Standard (AES).
These two early capabilities, DVP and DES, suffered from a smaller geographic operating range than the analog voice product, meaning that if you wanted DVP or DES you had to be closer to the repeater (or you needed more repeaters) than if you were using an analog radio. In the early 1980s a technical report was issued by the Federal Bureau of Investigation that indicated the range loss for the DVP and DES products would require nearly double the number of repeaters to match the coverage area of an equivalent analog system.
In response to this and other complaints, Motorola introduced the XL modifications to each of the DVP and DES products. They also produced the Digital Voice International (DVI), which was designed for export outside of the United States and was much weaker than the domestic privacy systems.
To summarize, the five voice privacy offerings for standard Motorola radios are DES, DES-XL, DVP, DVP-XL and DVI-XL. Remember that no matter which product might be in use, the control channel of a Type I or Type II trunked system remains unencrypted and can be monitored.
EDACS Voice Encryption
Enhanced Digital Access Communications System (EDACS) is a trunking system originally developed by General Electric. Technically, EDACS itself is a radio trunking format capable of supporting several types of digital voice traffic in addition to analog. Some systems may even have a mix of different voice transmissions on the same system as users upgrade from older radios to newer digital units.
The first generation, from the mid-1980's, is termed Voice Guard and uses either DES encryption or a proprietary algorithm called VGE.
The second generation from the early 1990's has much better voice quality and is called AEGIS. Again, either DES or VGE could be used as the encryption algorithm, or AEGIS could be run with no encryption at all. Although running without encryption doesn't provide any additional protection, the mere fact that it is digital prevents scanner listeners from overhearing conversations.
The current generation, called ProVoice, has even better voice quality than AEGIS and can either be encrypted with VGE or DES, or run unencrypted.
Results from GE's digital voice systems show that their range is farther than analog voice, due primarily to the error detection and correction methods in use.
On-Line Scanner Manuals
Dan,I have a Radio Shack PRO-35 scanner that works fine but I lost the manual. Do you have any idea where I can find the instructions or a user guide for it?
Thanks,
Ray
If you've picked up a scanner at a hamfest or flea market it probably came without a user manual. Fortunately, the Internet is a good resource to locate information about that "vintage" receiver.
Radio Shack has support information for more than 100 scanners on their website, including all of their trunk-tracking units. You can find the master index at support.radioshack.com/support_electronics/2849.htm
Besides having manuals for all three variants of the PRO-92 (200-0522, 200-0522A and 200-0522B), they even have documentation going as far back as the crystal-controlled PRO-20.
The Hobby Radio Stop in Ohio offers numerous manuals from a variety of manufacturers, including one of my favorite old handhelds, the Bearcat 200XLT. The website can be found at www.bearcat1.com/owner.htm.
Tallahassee, Florida
Dan,The Tallahassee Fire Department responds to fire, rescue, and medical calls in and around the Tallahassee, Florida area. Over the last few years, the City of Tallahassee has instituted an 800 MHz Trunking System Motorola Type II-i), with the Fire Department as a regular user. The 800 system was built for coverage across Leon County, as the TFD is the primary countywide fire department. Volunteer Fire Departments dot the county's landscape, with some responding just inside the city limits.
I enjoy listening to the TFD on 154.190, as well as talkgroup 1200 (Dispatch). With my PRO-92, I set the VHF simulcast as my priority channel and then I am free to listen to other public safety agencies on 800 MHz. The 800 system is growing, due to Florida Highway Patrol having talkgroups on the system, as well as the recent addition of the Leon County Sheriff's Department (requiring more frequencies).
Anyway, I just finished reading your article on simulcasting and thought I would add my thoughts.
Jay from Florida
Thanks for writing, Jay. I'm interested in hearing from other readers who are listening to simulcasts of systems that are currently or will be going digital.
That's all for this month. I welcome your electronic mail at dan@signalharbor.com, and as always more information is available on my website at www.signalharbor.com. Until next month, happy monitoring!